Do you search for 'unix file permissions essay example'? You can find all the information here.
For example, -rwxr-xr-- represents that the grouping has read (r) and execute (x) permission, but zero write permission. The last group of three characters (8-10) represents the permissions for everyone other. For example, -rwxr-xr-- represents that at that place is read (r) only permission.
Table of contents
- Unix file permissions essay example in 2021
- Rwxr--r-- permissions
- Unix permission numbers
- File permissions in linux with examples
- Chmod rw
- Rw-r--r-- permissions in linux
- Linux file permissions
- Unix read write permission
Unix file permissions essay example in 2021
 This image representes unix file permissions essay example.
This image representes unix file permissions essay example.
Rwxr--r-- permissions
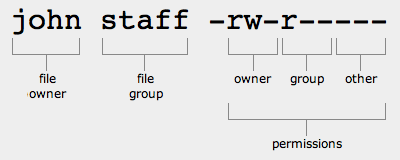 This picture shows Rwxr--r-- permissions.
This picture shows Rwxr--r-- permissions.
Unix permission numbers
 This picture illustrates Unix permission numbers.
This picture illustrates Unix permission numbers.
File permissions in linux with examples
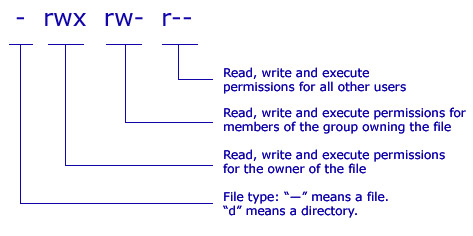 This picture illustrates File permissions in linux with examples.
This picture illustrates File permissions in linux with examples.
Chmod rw
 This picture shows Chmod rw.
This picture shows Chmod rw.
Rw-r--r-- permissions in linux
 This picture illustrates Rw-r--r-- permissions in linux.
This picture illustrates Rw-r--r-- permissions in linux.
Linux file permissions
 This picture demonstrates Linux file permissions.
This picture demonstrates Linux file permissions.
Unix read write permission
 This picture illustrates Unix read write permission.
This picture illustrates Unix read write permission.
What are the flags for file permissions in Unix?
The flags in the first column specify the file mode and the different sets of permissions: – : indicates that the user does not have read permission. r: indicates that the user has read permission. – : indicates the user does not have write permission. w: indicates the user has to write permission.
How are write and execute permissions used in Unix?
Write permission allows the user to modify the contents of the file. And execute permission allows the user to run the file as a program. In case the file is a directory, read permission allows the user to list the contents of the directory.
What are the different permissions for a file?
1 The read ( r) permission lets users look ( ls) into directories. 2 The execute ( x) permission lets users move ( cd) into directories. 3 The write ( w) permission lets users add and remove files.
What are the three levels of permissions in Unix?
Unix Permissions: File Permissions with Examples Access to a file has three levels: Read permission – If authorized, the user can read the contents of the file. Write permission – If authorized, the user can modify the file.
Last Update: Oct 2021
Leave a reply
Comments
Jecenia
24.10.2021 04:25The ' d ' at position 0 denotes the eccentric of file, information technology is either A ' d ' if the particular is a directory or ' cardinal ' if IT is a connectedness or it could just be A regular file. The phrase structure for renaming A file.
Royal
25.10.2021 09:01Estimated reading time: 3 minutes table of contents. How to find out the file character of a fil.
Suda
22.10.2021 06:36Fashionable terminal go to file manager. Note that some of these commands are different on non-solaris machines - see sunos differences.
Elease
26.10.2021 04:09Modification a file to be modifiable for user and legible for group and other. > sed '1d' file unix felt hat debian ubuntu.